导入.dump文件,运行!anaylyze -v
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
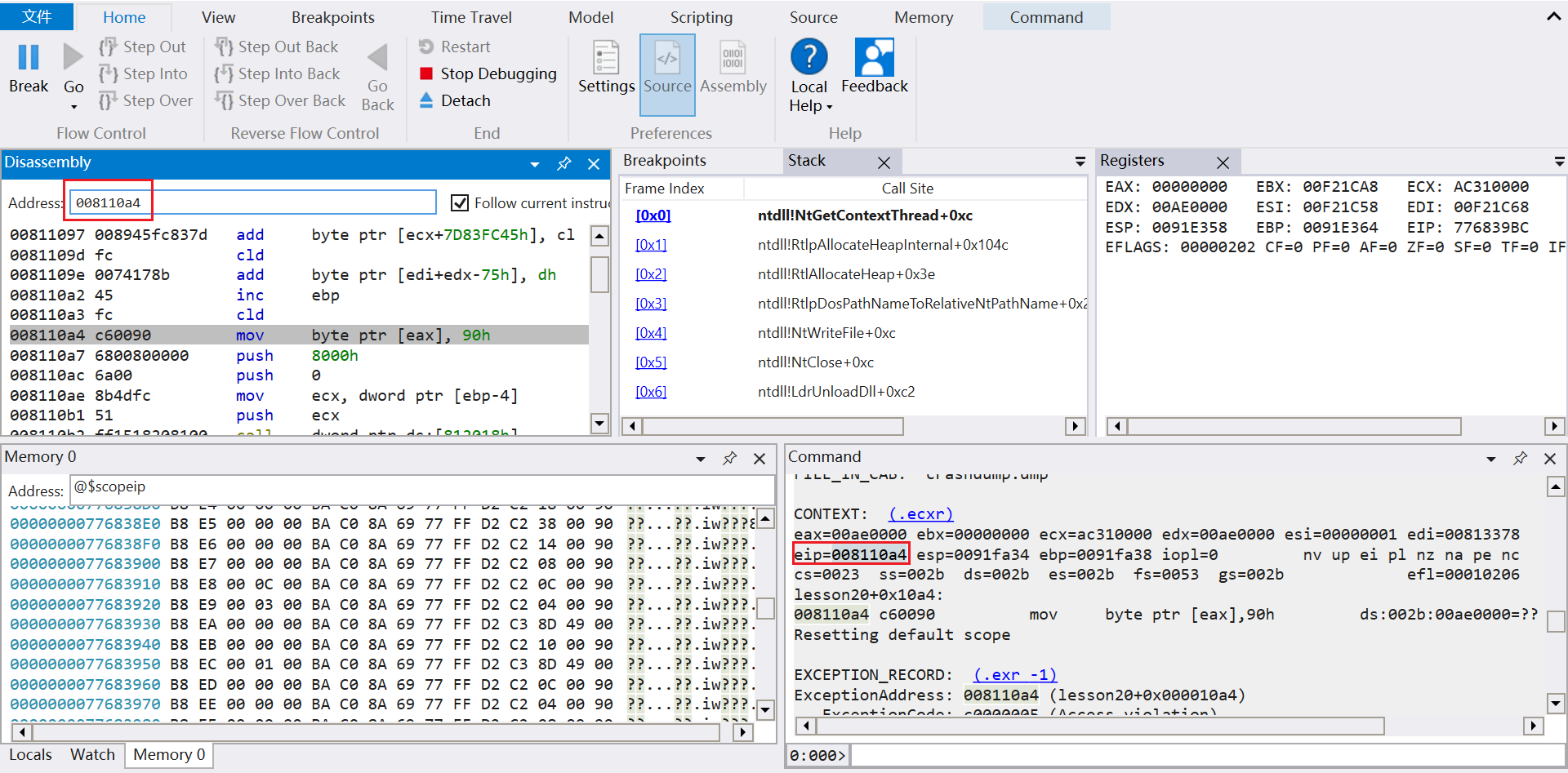
| 0:000> !analyze -v
*******************************************************************************
* *
* Exception Analysis *
* *
*******************************************************************************
// 下面的键值对展示了一些异常的关键信息
KEY_VALUES_STRING: 1
// AV:Access Violation
Key : AV.Fault
Value: Write
Key : Analysis.CPU.mSec
Value: 546
Key : Analysis.Elapsed.mSec
Value: 700
Key : Analysis.IO.Other.Mb
Value: 0
Key : Analysis.IO.Read.Mb
Value: 0
Key : Analysis.IO.Write.Mb
Value: 0
Key : Analysis.Init.CPU.mSec
Value: 249
Key : Analysis.Init.Elapsed.mSec
Value: 6055
Key : Analysis.Memory.CommitPeak.Mb
Value: 56
// 展示报错原因,无效指针操作,但未能定位到具体代码
Key : Failure.Bucket
Value: INVALID_POINTER_WRITE_c0000005_lesson20.exe!Unknown
Key : Failure.Hash
Value: {e0ccc258-0eae-4f80-eb69-527263cddced}
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Version
Value: 10.0.19041.1
FILE_IN_CAB: crashdump.dmp
// 程序崩溃时的寄存器信息。通过eip寄存器的值可以直接定位程序崩溃时的运行位置
CONTEXT: (.ecxr)
eax=00ae0000 ebx=00000000 ecx=ac310000 edx=00ae0000 esi=00000001 edi=00813378
eip=008110a4 esp=0091fa34 ebp=0091fa38 iopl=0 nv up ei pl nz na pe nc
cs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010206
lesson20+0x10a4:
008110a4 c60090 mov byte ptr [eax],90h ds:002b:00ae0000=??
Resetting default scope
// 异常记录包括以下内容
EXCEPTION_RECORD: (.exr -1)
// 异常地址
ExceptionAddress: 008110a4 (lesson20+0x000010a4)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
// 参数
NumberParameters: 2
Parameter[0]: 00000001
Parameter[1]: 00ae0000
Attempt to write to address 00ae0000
PROCESS_NAME: lesson20.exe
// 发生写入访问冲突的地址
WRITE_ADDRESS: 00ae0000
ERROR_CODE: (NTSTATUS) 0xc0000005 - 0x%p 0x%p %s
EXCEPTION_CODE_STR: c0000005
EXCEPTION_PARAMETER1: 00000001
EXCEPTION_PARAMETER2: 00ae0000
// 堆栈记录
STACK_TEXT:
WARNING: Stack unwind information not available. Following frames may be wrong.
0091fa38 008110e1 0091fa84 00811263 00000001 lesson20+0x10a4
0091fa40 00811263 00000001 01051878 010518f8 lesson20+0x10e1
0091fa84 7595fa29 0064a000 7595fa10 0091faf0 lesson20+0x1263
0091fa94 77677b5e 0064a000 04743c78 00000000 kernel32!BaseThreadInitThunk+0x19
0091faf0 77677b2e ffffffff 77698c81 00000000 ntdll!__RtlUserThreadStart+0x2f
0091fb00 00000000 008113ab 0064a000 00000000 ntdll!_RtlUserThreadStart+0x1b
STACK_COMMAND: ~0s; .ecxr ; kb
SYMBOL_NAME: lesson20+10a4
MODULE_NAME: lesson20
IMAGE_NAME: lesson20.exe
FAILURE_BUCKET_ID: INVALID_POINTER_WRITE_c0000005_lesson20.exe!Unknown
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x86
OSNAME: Windows 10
FAILURE_ID_HASH: {e0ccc258-0eae-4f80-eb69-527263cddced}
Followup: MachineOwner
---------
|
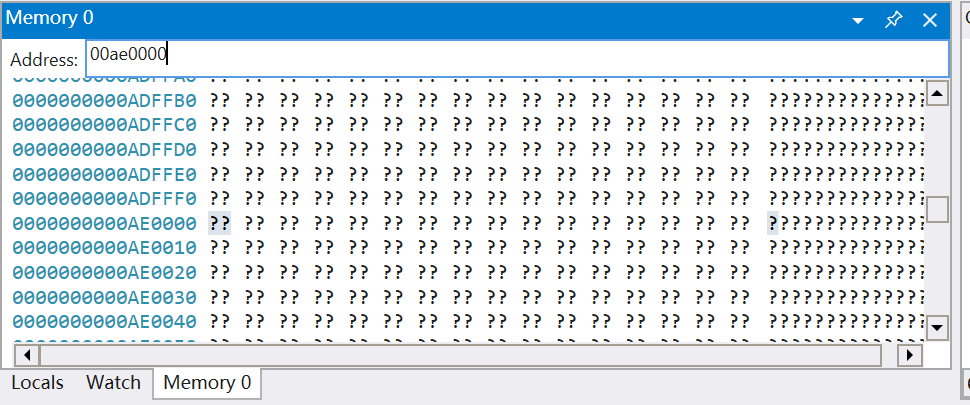
通过内存选项卡也可以看到,00ae0000位置并未分配内存。确定程序的崩溃是由于空指针操作导致的。